subtitled: What happened to the SBS Connection Manager?
VPN name resolution is a common problem for many IT folk. I have addressed in in previous blogs by manually configuring the VPN client to point to the corporate server for DNS, and adding the corporate domain suffix. This is not practical as it has to be done on every computer on which the VPN client was configured.
Small Business Server 2003 had a very nice little wizard that would create a deployable VPN client called “Connection Manager” which contained server connection information and allowed for proper name resolution over the VPN. Though the missing feature from subsequent SBS versions inspired this article, it can be used to create a deployable VPN client for any Windows Server. The SBS wizard basically ran a mini version of a standard Windows tool called CMAK.
Firstly you need to install CMAK, the Connection Manager Administration Kit. To do so, on a 2008 or newer server, open Server Manager under Administrative Tools, choose Features, and Add Features. In the features wizard choose Connection Manager Administration Kit, and complete the wizard.
Though there are many configurable options and features that can be added with CMAK, for the purposes of this article only the basics will be configured to allow for VPN name resolution, automatic installation, and to try to replicate the old SBS 2003 Connection Manager experience. One of the additional advantages of the Connection Manager Client is it limits the options with which the client can “tinker”, thus reducing support calls and increasing security.
In this example CMAK is being run on a 64bit machine. The deployable VPN client created can only be used on other 64bit machines. If you need to deploy on a 32bit machine you will need to install and run CMAK on a 32bit computer/server. CMAK may not available from the built-in windows options on older operating systems. If so, it can be downloaded as part of the Windows Server 2003 Administration Tools Pack (32bit) http://www.microsoft.com/download/en/details.aspx?displaylang=en&id=16770
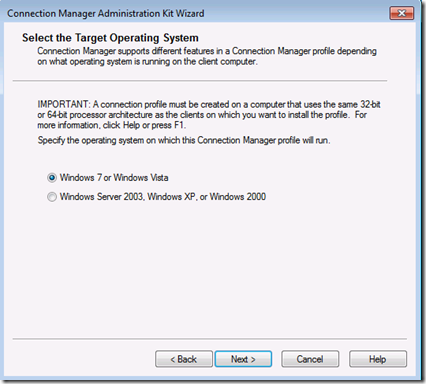
Start The Connection Manager Administration Wizard from Administrative Tools, accept the UAC warning, click next, and select the O/S on which the client will be deployed, remembering the above warning about 32/64 bit.
Select New Profile,
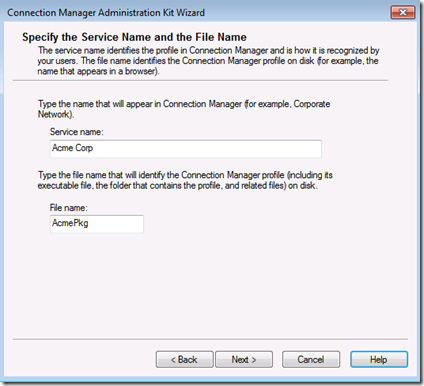
Enter a ‘Friendly’ name for the connection and a file name (<9 characters) for the deployment package.
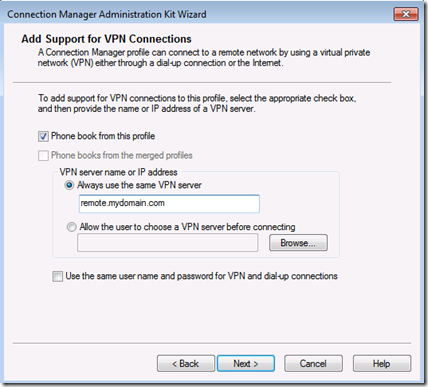
Rather than cluttering this post with unnecessary images, accept the defaults on the next two pages, “do not add a realm name to the user name” and leave the merge profiles boxes empty. In the next window, as per the image below, check Phone book from this profile, always use the same VPN server, and insert the public FQDN or IP of the VPN server.
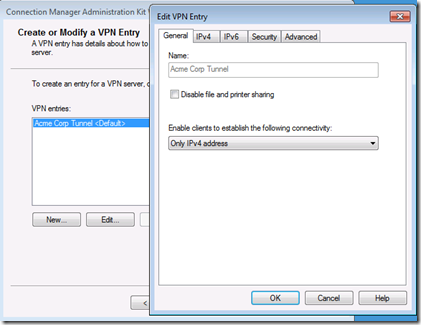
Next highlight your new connection and choose edit. Under General select Only IPv4 addresses. If you like, for added security you can disable file and printer sharing, which blocks access to shares on the connecting client’s computer while connected to the VPN.
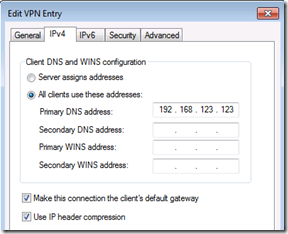
Under IPv4 add the internal IP for your corporate DNS server. If you have multiple corporate DNS servers you can add a second, and if you have WINS servers you can add those as well. Do not add public DNS servers here. I recommend checking “Make this connection the client’s default gateway” (disabling split-tunneling) which blocks access to to the client’s local LAN while connected to the VPN. By doing so Internet access is actually made via the VPN, rather than through the local router. One reason you may need to un-check this is it also blocks access to a local networked printer, i.e. one that is not physically attached to the connecting computer. Leave “Use IP Header compression” checked. Note that in a user created VPN client using the tools built into a Windows PC, the “default gateway” option can be changed. When created with CMAK it cannot be changed. This is intentional for security reasons. Split-tunneling, allowing the client simultaneous local and remote network access, is considered a security risk.
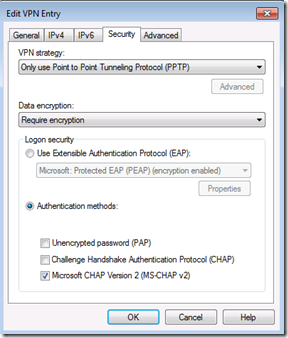
Under security you can leave the defaults or change to “Only use Point to Point Tunneling Protocol (PPTP)”. If you are connecting to an old server it may also be necessary to also check CHAP authentication, but this is less secure than MS-CHAP v2, so only do so if absolutely necessary. All 2008 and newer servers use MS-CHAP v2 by default.
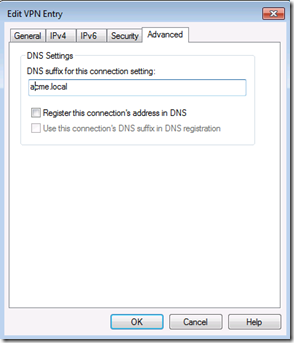
Under advanced add the internal corporate domain suffix. Check “Register this connection’s DNS address in DNS” if for some reason LAN clients need to resolve the name of the remote computer. I recommend not doing so if not needed as it adds unnecessary entries to DNS that may not be cleaned up if DNS scavenging is not properly configured. Select OK, Next, and move on to the next window.
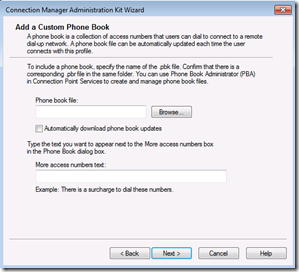
We are not using “phone books” so uncheck “Automatically download phone book updates”
From here accept all defaults in the next 4 windows; Configure Dial-up Networking, Specify Routing Tables, Configure Proxy Settings, and Add Custom Actions.
Note: it is assumed the server VPN configuration is basic, assigning IP’s in the same subnet for VPN clients as LAN clients, which is typical of SBS. However, if the VPN clients are assigned addresses outside of the LAN subnet, and you want to access resources on the corporate LAN other than the VPN server, you will need to add a routing table file, on the “Specify Routing Tables” page, to have the route pushed out to VPN clients.
Though not necessary at all you may want to add a custom graphic or logo to the connection client. This is done on the “Display Custom Logon Bitmap” page followed by the ability to add a custom graphic in the phone book (list of connections), and on the 3rd related page you can choose to use custom Icon for the deployed VPN connection.
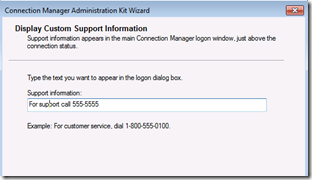
Leave the “Include Custom Help File” as default, and under “Display Custom Support Information”. You may want to add contact information. This is displayed on the VPN connection client where they enter their user name and password, when trying to establish a connection.
Accept the defaults in the remaining windows; “Display a Custom License agreement” and “Install Additional Files…”. In the final Window “Build the Connection Manager Profile and its Installation Program” leave Advanced uncheck, and assuming you do not wish to make any changes, click Next, and Finished. The deployable package will be saved in a folder named profiles in the CMAK folder, the default location being: C:\Program Files\CMAK\Profiles\Windows 7 and Windows Vista\ You only need to copy the .exe file to the client computer, in this case AcmePkg.exe
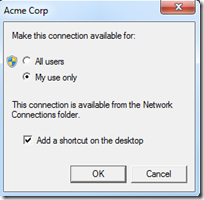
To configure the client, simply double click on the .exe file. You will be prompted if you want the client to be available to all users or just the current user.
Click OK, and wizard will complete, add a connection icon to the desktop, add the connection to task bar network icon………
…….and launch the VPN client.
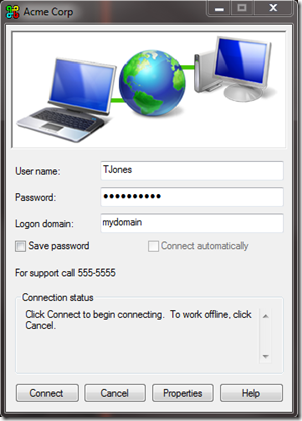
If you wish to connect enter the user name of a member of your VPN User group, their password, and internal domain name. The domain name does not have to be present just to connect to the VPN, but in most cases if the PC is not domain joined, it needs to be there to access files using server names, rather than IP’s.
You should now have access to resources on the remote server, assuming the VPN at the server end is properly configured, and you have the appropriate Share and NTFS/Security permissions on the server to do so.
If needed, I have bloged in the past about configuring the VPN server.
Configuring a Windows SBS 2003 as a RRAS/VPN Server
SBS 2011 Essentials – Configuring VPN access
Configuring a Windows 2003 RRAS/VPN Server with 1 network adapter




Comments on: "Windows VPN Client Deployment" (3)
$author you have amazing/great/awesamblog
[…] https://blog.lan-tech.ca/2012/01/30/windows-vpn-client-deployment/ Rate this: Like this:LikeBe the first to like this post. […]
Finally someone that gives advice in words I can comprehend.