Following is an outline as to how to configure a Cisco ASA 5505 for an SBS 2008/2011 network, including basic router configurations, IP addressing, and port forwarding, using the GUI/ASDM. The ASDM version used at the time of writing is 6.4(5), and ASA Version 8.2(5). For the record this can be accomplished much more easily from the CLI/Command Line Interface, but we SBS folk tend to like to do things from a GUI. I will however post a follow-up article outlining how to do so from the CLI, using only a handful of commands. [Updte: for CLI instructions see: https://blog.lan-tech.ca/2012/01/25/configure-cisco-asa-for-sbs-20082011-network-using-cli/ ]
It is assumed the ASA is still set to factory defaults. If so, skip to “Basic Router configuration”.
Reset to factory defaults:
Since this article is dedicated to using the ASDM console, to reset from within, simply log on, select “File” from the menu, and then “Reset Device to the Factory Default Configuration”. If you do not have access to the ASDM console, i.e. you do not know the IP, you can use the blue console cable and access through Telnet. Once connected to the CLI (Command Line Interface) enter the following commands:
- enable
- config t
- config factory-default (press the space bar a few times when “more” is displayed to get back to the prompt)
- reload save-config noconfirm (to write to flash memory)
- the unit will reboot with factory defaults
Basic Router configuration:
We will run the Start up Wizard to do the basic configuration. During the process do not make changes to the internal interface IP or Internal DHCP settings.
Launch the ASDM using https://192.168.1.1 , choose to ignore the certificate error, and select “run Startup Wizard”. When prompted for a username and password leave both blank. You can also start the wizard from within the ASDM from the menu under Wizards, Startup Wizard.
[ Edit: In case it is confusing; after publishing it was pointed out you can see the 192.168.111.254 current ASA address in the title bar. Please ignore, it is unrelated to the configuration. ]
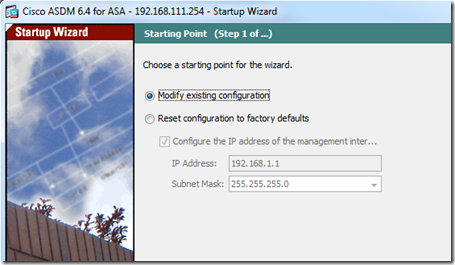
Starting Point: In the first window accept the default “modify existing configuration” and click next.
Basic Configuration: If you like you can change the ASA Host Name and domain, but I is not necessary. I strongly recommend changing the password, and make it secure. When you log back in later the user name will still be blank.

Interface Section: Leave all a defaults.

Switch Port Allocation: Again the defaults are fine for this configuration.

Interface IP Address Configuration: Presumably you have been assigned a static public IP by your ISP where you are running a mail server. If so select “Use the following IP address”, enter the appropriate IP and subnet mask under “Outside Address”. (Note: you will need to add a static route for the default gateway later)
If using DHCP with your ISP, select “Use DHCP” and check “Obtain default route using DHCP” (which will automatically add the default gateway). When using DHCP you will probably also want to set up a DDNS service. To do so see the following article: Using DDNS Services with SBS 2008/2011
The wizard will not allow you to continue without entering a DMZ address. You will not be using the DMZ in this configuration so simply pick a private IP outside of any subnet you plan to use, and select a subnet mask of 255.255.255.0, if presented with a DMZ related error you can ignore.

DHCP Server: We will deal with DHCP later along with the inside interface IP. Leave the current defaults “Enable DHCP” and the IP range for now.

Address Translation (NAT/PAT): You will want to use PAT, so accept the defaults.

Administrative Access: This determines from which IP’s or subnets you can access the ASA 5505 to manage it, and using which protocols. The current default is using the ASDM from the 192.168.1.0 subnet. If you plan to change the IP of the router to a different subnet you need to add it now, before making changes to the inside interface’s IP. Assuming you later plan to use 192.168.123.0/24 (/24 = subnet mask 255.255.255.0) for your local network, I recommend adding that subnet to the inside interfaces, using two rules, one for HTTPS/ADSM and the other for Telnet, by clicking the “edit” button”. Leave the “Enable HTTP server for HTTPS/ASDM access to this ASA” checked near the bottom.

Startup Wizard Summary: This page displays a summary of your choices. Review and click finish.

Disable DHCP: Assuming you are running SBS 2008/2011 Standard and not SBS 20011 Essentials, you will need to turn off DHCP on the inside interface of the Cisco as the SBS server should most definitely be the DHCP server. If not convinced see: Do I absolutely have to run DHCP on SBS 2008? If running SBS Essentials the default is to have the router as the DHCP server, though it does not have to be. To disable DHCP, log back into the ASDM if you are no longer connected, and navigate to; Configuration | Device Management | DHCP | DHCP Server | highlight the inside interface and click Edit” | uncheck “Enable DHCP server”. Then click OK and Apply at the bottom.

Change Inside interface (LAN) IP: As mentioned earlier, for the purposes of this article we will use 192.168.123.x (properly represented as 192.168.123.0/24) and choose 192.168.123.254 as the router inside interface IP but for your configuration match the current subnet of your SBS server.
This will be the gateway IP for PC’s and servers on the SBS network. Navigate to: Configuration | Device Setup | Interfaces | Highlight the inside interface and select Edit and change the IP to that of your choosing. Click OK, then check the box “ Enable traffic between two or more hosts connected to the same interface” at the bottom, and Apply.
Note: Should you choose to enable a VPN, using the Cisco or the SBS built-in VPN, the site from which a client connects, must use a different Network ID (Subnet) than that of the SBS LAN. As a result, nobody connecting from a remote site that uses 192.168.1.x locally can connect to resources on this network. Therefore it is always a best practice to avoid common subnets like; 192.168.0.x, 192.168.1.x, 192.168.2.x, 192.168.100.x 10.0.0.x, and 10.10.10.x. However if your SBS is already configured you would need to change the network addressing for the entire network. In the event you were to choose to do so make sure you use the wizard for changing the server IP located under SBS console | networking | Connectivity | Connect to the Internet. You also have to change any DHCP scopes, reservations, exclusions and device with statically assigned IP’s such as printers.

Add a static route for the router’s default gateway: As mentioned before if you have with a static public IP assigned to the outside interface, you also have to create a static route to assign a default gateway to allow the router Internet access. To do so select Device Setup | expand routing | Static Routes | and on the right click Add. Select the outside interface, choose “any” for the Network from the drop down list and insert the gateway address assigned by the ISP, with a metric of 1. The remaining items should retain the default settings. Click OK and Apply.

If you have not already done so, I would recommend saving all changes at this point by selecting from the menu File and then “Save running configuration to flash”, or at ant point simply press Ctrl+S to save.
Configure port forwarding:
SBS requires several ports be forwarded for various services. Below is an outline as to how to configure port forwarding for SMTP (port 25). You will need to do this for each of the services in the following list that you plan to use:
- SMTP port 25 Exchange
- HTTPS / SSL port 443 Outlook web Access, Remote Web Workplace (Remote Web Access), and SharePoint
- SharePoint custom port 987 (SBS 2003 not required)
- RWW & Sharepoint 4125 (SBS 2003 only, not required for SBS 2008/2011)
- PPTP port 1723 SBS VPN. The Cisco VPN is far more secure and moves authentication to the perimeter of the network. Far better to use it than the SBS VPN since it is included with the ASA 55050
- RDP port 3389 (Definitely not recommended. Much safer to use RWW/RWA)
Add a NAT Rule: Login into the ASDM, remembering to use the new IP address of the router. Navigate to Firewall | NAT Rules. on the right under addresses there is an option to +Add, select this and then Network Object. Enter the name of the Object, in this case the SBS, enter the IP (in our example 192.168.123.10) and a subnet mask of 255.255.255.255. (Adding a network object is not completely necessary but makes reviewing configurations at a later date easier to understand as items are referenced by name rather than IP)

Next in the same Window, under “Configuration > Firewall NAT Rules” in the tile bar, click +Add and select Add Static NAT Rule. In the resulting window set the “Original” Interface to inside and next to source click the drop down list button. Select your new object (SBS-Server in this example). Set “Translated” Interface to outside, and check the box to “use interface IP address”. Select Enable Port Address Translation (PAT), TCP, and enter either the port number, or in the case of most services you can enter the service name, if it is known to the Cisco router. A drop down list of known service will appear when you start to type the service name if one exists. If using non-standard services, enter the port number using the format tcp/987. The Original and Translated ports in this case should be the same.
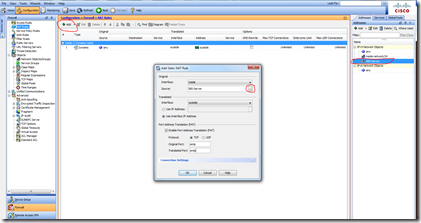
Click OK and this will add the rule to the list of static rules.

Add an Access Rule: Next, again in the firewall section, Navigate to Access Rules | Add | Add Access Rule. Change the Interface to Outside, the Source will be “any”, Destination the outside interface, Service can again be selected from the drop down list, and add a description if you like. Leave the “More Options” section set to defaults. Click OK and Apply.

Repeat the above steps for all services you will be using, probably HTTPS/443 and SharePoint/987, and don’t for get to save ( Ctrl+S) when complete.
This should complete the SBS requirements.
Additional Features you may wish to enable:
- To enable pinging of internet IP’s from the LAN for testing, navigate to: Configuration | Firewall | Service Policy Rules | highlight the policy under Global Policy and click edit | Rule Actions | check the box for ICMP | click OK and Apply.
- To allow Tracert to internet IP’s, add the ICMP rule above, then while still under the Firewall configuration switch to the Access Rules item click Add | Add Access Rule | then set the interface outside, action is Permit, and Source/Destination is any. Under Service, enter icmp, it should auto-fill or you can use the drop down list line and click OK. Click OK again in the Add Access Rule dialog and Apply the results to finish the process.