There are already dozens of articles relating to configuring Microsoft’s Hyper-V Server 2008 R2 (the free core version), however a colleague’s intimidation of command line server management inspired me to post my notes to ease his mind and perhaps those of a few readers as well. Yes, it is a command line only version of server 2008 R2, with only a 15 line/option GUI to assist with the most basic configurations……..

Yet, after some minor configuration and enabling some basic services, you can manage the server in a very similar way you would manage others servers with; Hyper-V Manager, administrative tools, remote access, a file explorer, and even a web browser.
It is worth noting that there are definite advantages to using this version of Hyper-V. It is free, it supports more than 32GB of RAM (server 2008 R2 standard does not, you need Enterprise or Datacenter editions), smaller footprint, and a somewhat limited attack surface.
Notes:
- I am assuming Hyper-V core is successfully installed and you are at the point of configuring, if not the following links may help you get to this point Test Hyper-V compatibility, Step-by-Step Guide to Getting Started with Hyper-V
- The assumption in this configuration is the Domain Controller and DNS server will be a virtual machine on the Hyper-V host. As a result it is recommended the Hyper-V host is not joined to the domain as no domain logon server will be available until after the guest VM has been started.
- “Management PC” refers to the PC, or server, from which you wish to manage the Hyper-V host
- All command line entries below, on both server and management PC, must be done from an elevated command prompt. On the server the default is elevated, which is confirmed by the “Administrator” on command window title bar
Server Configurations (Hyper-V host):
Run native Hyper-V GUI configuration tool:
- The configuration tool (as in image above, should automatically start at logon but if not, from a command line, enter sconfig
- Item #1: Leave as a workgroup
- Item #2: Enter the computer name
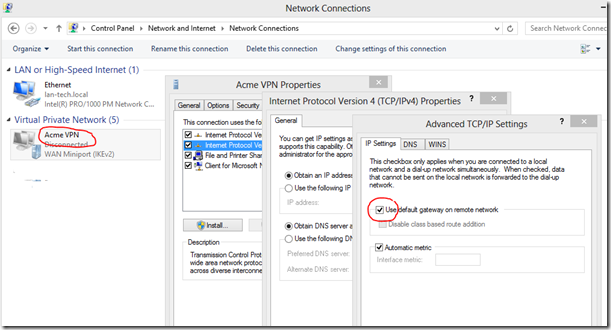
- Item #8: Configure the network: Use a static IP. I recommend at least primary server be an internal DNS server, secondary an ISP. (Keep in mind on a domain joined server/PC you should not combine internal and public DNS servers, but this is not domain joined). Best practices suggests 2 NIC’s should be enabled, one for management and the other for use by VM’s, though this is not necessary.
- Item #9: Set date and time
- Item #5: Set Windows update settings auto or manual.
- Item #6: Download and install all updates, reboot as necessary
- Item #3: Add any local admin accounts. I recommend adding new account with a name matching the login account of the remote management PC. The names must match for some services to work.
- Item #4: Configure remote management by enabling sub-options 1 to 3
- Item #7: Enable remote desktop access (note this is still command line only)
- Item #15 Exit to a command line
DNS:
As stated the Hyper-V machine is not a member of the domain, therefore it is recommended the following additions be made to assist with name resolution
Use the Hosts file to allow the Hyper-V host to resolve the name of the management PC. From an elevated command prompt , open the Hosts file using Notepad by entering: notepad c:\Windows\System32\drivers\etc\hosts . Add a record in the Hosts file for your management PC/s using
IP <tab> Pc’s DNS name <tab> # a note (optional) <enter>
eg: 192.168.123.123 PCname.MyDomain.local # management PC
(Note: it is very important hit return, after every entry including the last line, and then save. For more information about Hosts and Lmhosts files, and their syntax see: https://blog.lan-tech.ca/2012/04/26/hosts-and-lmhosts-files/
Add the domain suffix to the domain search list within the registry to further assist with DNS name resolution. Start the registry editor using regedit and locate the following registry key:
HKLM\System\CurrentControlSet\Services\TCPIP\Parameters\SearchList
Then add your domain suffix such as mydomain.local (separate multiple suffixes, if needed, with commas)
Permissions:
To configure additional permissions on the Hyper-V host download Hvremote.wsf from: http://archive.msdn.microsoft.com/HVRemote to a USB drive or CD. Then from a command line copy HVremote to local directory such as Temp folder. DOS commands are as follows (assume HVremote is on a USB drive labeled D:
cd\
md Temp
copy D:\FolderName\hvremote.wsf C:\Temp\hvremote.wsf
Run the following commands from the directory where hvremote is located to grant Hyper-V administrators the necessary permissions to do so. This asdds the admin to the “Distributed COM User’s group”. Again from an elevated command prompt, run the following command using the user you created under Item #3 above in the initial configuration GUI.
Cscript hvremote.wsf /add:user
If this is the first time hvremote has been used to add a user a reboot may be required
Firewall:
The necessary firewall exceptions should have been enabled by Item #’s 3 & 7 above. You may also want to be able to ping (IPv4) the server for testing. To do so from a command line enter:
netsh firewall set icmpsetting 8
Or use the new command for “Windows Firewall with advanced Security”
netsh advfirewall firewall add rule name=”ICMP Allow incoming V4 echo request” protocol=icmpv4:8,any dir=in action=allow
(Note: if cutting and pasting the above command, you will have to substitute the quotation marks using your keyboard. This site’s/font’s quotation marks are not standard ascii characters)
For additional firewall information relating to pings see: http://dpotter.net/technical/2010/02/enable-ping-on-windows-server-2008-2/
Management PC Configurations:
DNS:
If the PC is a member of a domain, you can add a Host (A) record to the DNS management console for the Hyper-V host, or you can make an entry in the management PC’s Hosts file similar to the instructions for the server. This will ‘point’ this to the server such as:
IP <tab> Server’s DNS name <tab> # a note (optional) <enter>
eg: 192.168.123.123 HVServerName.MyDomain.local # Hyper-V host
Permissions:
As on the Hyper-V host, download HVremote from http://archive.msdn.microsoft.com/HVRemote or copy from your USB Key to a local directory as below:
cd\
md Temp
copy D:\FolderName\hvremote.wsf C:\Temp\hvremote.wsf
Using an elevated command prompt run the following commands from the directory where HVremote is located. Where the Hyper-v host is not part of the domain you must enable anonymous DCOM access using:
Cscript hvremote.wsf /mode:client /anondcom:grant
This one command must be run from an non-elevated command line:
Cmdkey /add:ServerComputerName /user:ServerComputerName\UserName /pass:UserPassword
Firewall:
There are 4 Hyper-V Management Client firewall exceptions that need to be enabled. Running the following command, from an elevated command prompt, will do so:
Cscript hvremote.wsf /mode:client /FirewallHyperVClient:Enable
You also need allow rules for MMC exceptions (management consoles) which can be applied with:
Cscript hvremote.wsf /mode:client /mmc:enable
If you have other 3rd party firewall software installed, you need to manually configure it with the same exceptions.
If you wish to use the Disk Management component of the Computer Management MMC for the remote host, you need to enable the inbound “Remote Volume Management – Virtual Disk Service Loader (RPC)” exception with:
netsh advfirewall firewall set rule name=”Remote Volume Management – Virtual Disk Service Loader (RPC)” new enable=yes
You also have to set the “Virtual Disk service” on the Hyper-V server to Automatic and start it.
sc config vds start= auto
sc start vds (not needed if rebooting – will automatically start)
Reboot:
To apply all changes a reboot of the PC is recommended.
Testing connectivity:
When complete test and review the output using the commands below. For details and troubleshooting download the documentation for HVRemote from: http://archive.msdn.microsoft.com/HVRemote
From the server:
Cscript hvremote /mode:server /show /target:clientcomputername
From the client PC:
Cscript hvremote /mode:client /show /target:ServerComputerName
Remote Management Tools:
RSAT tools:
Download and install RSAT (Remote Server Administration Tools) on the management PC making sure you have the RSAT version compatible with that PC’s operating system. The link for Win7 SP1 is below. With these tools you can now connect the Hyper-V host and manage it from a PC using all those familiar tools like Computer Management, Disk Management, Windows Firewall with Advanced security, Task Sheduler, etc., and of course the most important; Hyper-V manager which will allow you to create and manage your VM’s the same as you would if you had the full GUI version of Server 2008 R2 as a host.
http://www.microsoft.com/download/en/details.aspx?id=7887
Remote Console (RDP):
You can access the Hyper-V console (still command line only) using a standard RDP connection. You can also install “Portable Apps” which you can then run from an RDP session. See further down in this list of Remote management tools.
Mstsc -v:<Hyper-V host name>
Portable Apps:
You can run standard “portable apps” on the console, or during a remote desktop session such as:
Windows Explorer Equivalent A43:
http://www.alterion.us/a43/index.html
Firefox Web Browser (for security reason web browsing from the host is not recommended):
http://portableapps.com/apps/internet/firefox_portable
Others:
http://www.portablefreeware.com/all.php
Powershell:
To remotely run PowerShell you will need Powershell 2. which is available from Windows updates. To install and enable please see the following article http://geekswithblogs.net/twickers/archive/2009/11/04/136013.aspx With it from the Host console, or remotely, you can manage many services using scripts/cmdlets from:
http://pshyperv.codeplex.com/
Others:
http://www.portablefreeware.com/all.php
PSExec:
PSExec is a tool developed by Sysinternals, now Microsoft that allows you to run DOS commands on remote machines:
http://technet.microsoft.com/en-us/sysinternals/bb897553
Hyper-V Monitor Gadget:
A great desktop gadget for monitoring the status of your Hyper-V servers, status and perfomance, as well as the ability to start and stop. Requires permissions and services as outlined earlier.
http://hypervmonitor.codeplex.com/

Additional Resources:
Configure Hyper-V Remote Management in seconds
http://blogs.technet.com/b/jhoward/archive/2008/11/14/configure-hyper-v-remote-management-in-seconds.aspx
Full HVRemote documentation and download:
http://archive.msdn.microsoft.com/HVRemote/Release/ProjectReleases.aspx?ReleaseId=3084
Install and Configure Hyper-V Tools for Remote Administration
http://technet.microsoft.com/en-us/library/cc794756(WS.10).aspx
How to use the “netsh advfirewall firewall” context
http://support.microsoft.com/kb/947709
How to Enable Remote Administration of Server Core via MMC using NETSH
http://blogs.technet.com/b/askds/archive/2008/06/05/how-to-enable-remote-administration-of-server-core-via-mmc-using-netsh.aspx